10 Simple Techniques For Kdit Services

Voice over web protocol is a functional interaction method in which individuals within a company can make calls as well as send messages or get them through web links as opposed to typical landline phones. Vo, IP does more than a normal phone line, such as voicemail, call forwarding, video clip conferences, as well as loads a lot more.
The 2-Minute Rule for Kdit Services
It permits firms to access the solutions of a Vo, IP company and get IT support, both on-site and also remote support. The IT aid workdesk assistance is a kind of service that helps in helping as well as supplying customers with technological assistance. When an individual comes across a concern relevant to any software application or hardware, they send a request to the IT provider, who settles the issue either from another location or through on-site help.
Any problems that are found will be repaired immediately by the IT support team without disturbance to the procedures of business. Data and also details backup solutions are satisfied business' demands for shielding their sensitive data from being shed (KDIT Services). These expert solutions are suggests to stop data loss in instance of system failing, natural disasters, destructive assaults, or a power outage.
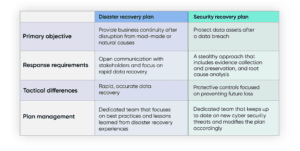
In today's digital globe, the demand for cyber safety and security is extra pressing than ever. Cyber hazards are unavoidable as well as can trigger tremendous damage to any type of service.
Rumored Buzz on Kdit Services
Moreover, they supply remedies to protect your systems in case of any cyber-attack or data breaches, such as building firewall softwares as well as other safety and security options. Software program as a Solution is a service version of software program distribution in which customers can access applications over the internet. IT service suppliers supply Saa, S solutions that are organized on their servers, making it simpler for services to make use of the most current as well as most innovative technologies without needing to buy any equipment or software application.
This makes it much easier for companies to concentrate on their core procedures and also activities without having to bother with the IT element. These IT services are brought on to sustain an organization in the advancement lifecycle as well as completion of a project. The provider will certainly give individuals with the comprehensive experience and also experience needed, which offloads the in-house IT teams as well as safeguards far better end results.
The provider will certainly likewise be accountable for supplying end-user technological assistance as well as upkeep services on the software developed. Up to your selection of solutions and also involvement, IT solution providers organize a committed team of adepts or include added personnel to your IT groups for even more extensive as well as cohesive assistance.
Indicators on Kdit Services You Need To Know
Outsourcing IT services to a provider enables organizations to concentrate on the core tasks of their business while the outsourced companions look after all various other technological tasks. This results in improved efficiency, much less stress and anxiety, and greater consumer satisfaction. Furthermore, because IT service suppliers have a team of professionals who focus on certain areas, they provide specific and customized remedies that are customized to the specific demands of a service.

During these times of cyber threats, all business must focus on the security of their information as well as details. IT company have substantial knowledge as well as experience in this area; they possess the right devices, methods, and also experience to safeguard any kind of organization against destructive assaults or various other disasters. With them aboard, businesses do not have to stress over anything pertaining to safety as it is all cared for.
If you are well planned for acquiring out your IT procedures, what you need to come up with following is a reputable and also capable IT companion the trick to success (KDIT Services). Why look where else while you got one right here Orient Software program? Discover why you must companion with us Not others, and reach out to us today.
The 6-Second Trick For Kdit Services
As a local business owner or supervisor, you recognize that fantastic IT services are necessary to keep your business running at peak efficiency. What you might not recognize are all of the Read More Here various IT service alternatives that your organization can capitalize on. When providing examples of IT services, many individuals will certainly think about software application updates and infection elimination.

Outsourcing IT services to a provider allows organizations to focus on the core tasks of their business while the outsourced partners care for all various other technological jobs. This leads to enhanced effectiveness, less anxiety, as well as higher client fulfillment. Since IT solution suppliers have a team of professionals that specialize in specific areas, they provide customized as well as personalized solutions that are customized to the certain read needs of an organization.
Getting My Kdit Services To Work

If you are well prepared for contracting out your IT procedures, what you require to come up with next is a trustworthy as well as capable IT companion the secret to success.
As a local business owner or manager, you recognize that excellent IT services are needed to maintain your company going for peak performance. What you might not know are every one of the various IT service alternatives that your company can make use of. When providing examples of IT services, many individuals will certainly consider software application updates and infection elimination.
All about Kdit Services
This guideline mentions that your data should be kept in three different locations: the resource tool (likely a computer system or workplace workstation), your local backup tool, and also an off-site area (ideally via a cloud back-up solution). Following the 3-2-1 backup rule guarantees that the likelihood of all 3 copies of your data being lost are slim to none.